In our digital world, where cyber threats are just a click away, data security is a big deal. Did you know that according to IDC, by 2025, the amount of records stored globally will skyrocket to a mind-blowing 175 zettabytes? That's a lot to protect!
Businesses, especially those in the second-hand device market, face this challenge head-on since they regularly deal with confidential materials. Any oversight can result in legal consequences, emphasizing the utmost importance of security.
Why Secure Data Destruction Is Important
Destruction refers to the irreversible removal. This can be achieved either by overwriting it with random characters or by physically destroying the storage medium. The goal is to make a recovery impossible.
For global enterprises, adhering to safety regulations is a legal obligation. Non-compliance can result in hefty fines and repercussions, along with loss of customer trust.

Seven Foolproof Data Destruction Methods
File Deletion and Disk Formatting
This basic approach involves removing files or reformatting the storage unit.
+ Quick and doesn't need specialized tools.
- With certain tools, removed information can be retrieved, posing a risk for sensitive content.
Overwriting Data
Replaces existing content with random characters or zeros multiple times.
+ Secure and allows the storage unit to be reused.
- Takes time, especially with multiple passes. Not work on damaged drives with inaccessible sectors.
Data Wiping
Clears a storage, ensuring it's irrecoverable.
+ Comprehensive and suitable for units like SSDs and flash drives. The device can be reused.
- Can be lengthy, especially for larger storage units.
Secure Erasure
Erasing data with special tools that follow specific security standards.
+ Meets many legal and compliance standards, ensuring thorough removal.
- Can be time-consuming for big volumes, requires specific tools.
Magnetic Degaussing
A machine produces a magnetic field that disrupts the domains on a storage unit, making it unreadable.
+ Quick and irrecoverable. Extremely safe when executed correctly.
- Needs degaussing tools. Hard drives can't be reused.
Physical Destruction
It involves tangible harm to the storage unit, like crushing or drilling.
+ Ensures content is irrecoverable.
- Not eco-friendly, contributing to electronic waste, expensive.
Shredding
Machines grind disks into small fragments.
+ Extremely secure, irrecoverable. Efficient for multiple devices.
- Not eco-friendly. The pieces often become waste unless recycled.
The Best Method
When deciding on a technique, keep in mind the following aspects:
- Speed: How fast do you need the process to go?
- Budget: What financial resources are allocated?
- Auditability: Is the process verifiable for compliance purposes?
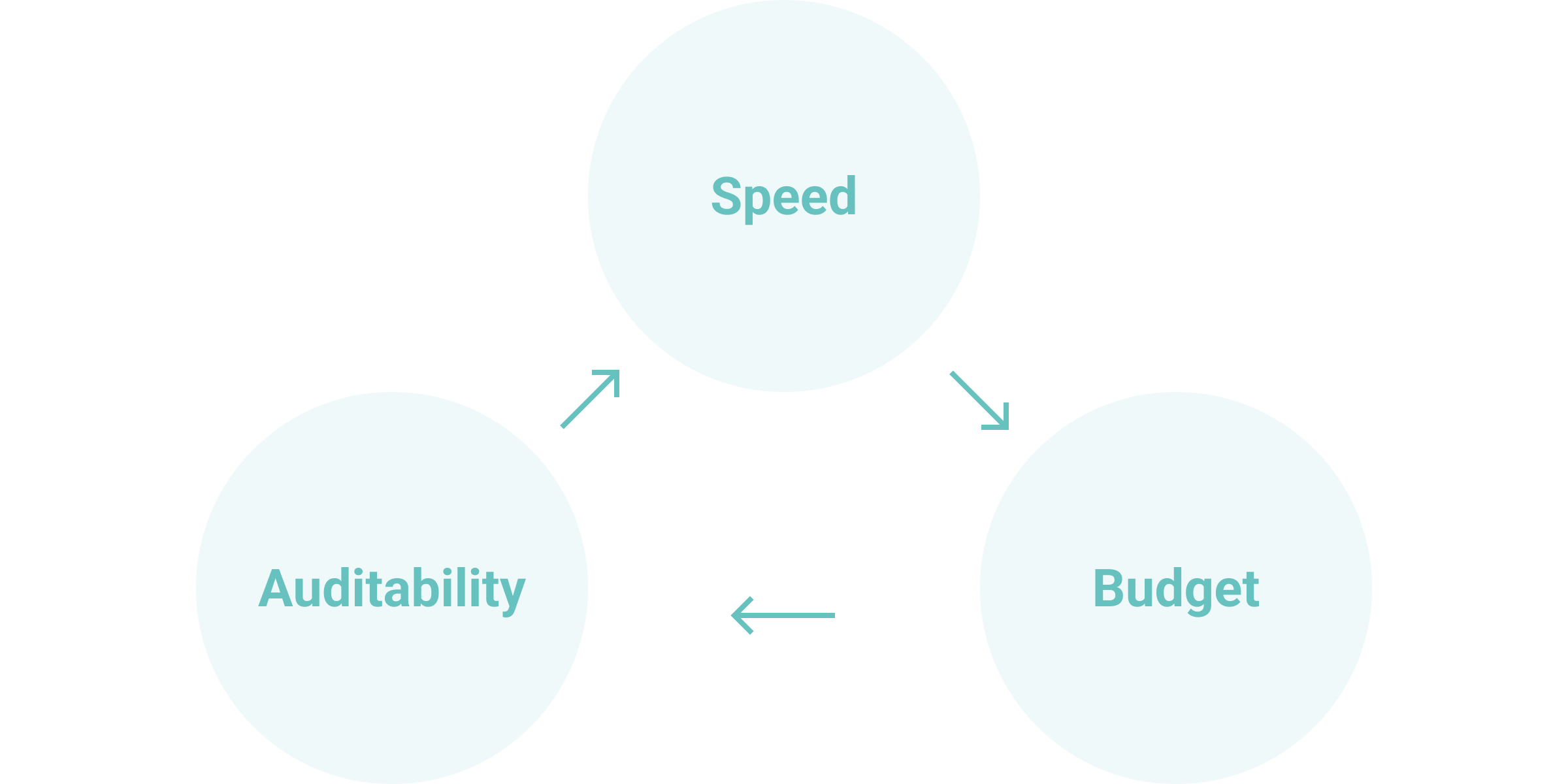
Within the realm of used smartphones, the main priorities are speed, affordability, and the potential for device repurposing. Given these factors, the secure data erasure technique might be the best fit. It ensures top-notch security and still permits the device's reuse, which can be a boon for businesses aiming to get the most out of their transactions.
Many conflate data destruction with the sanitization method. Data destruction is permanently deleting, either by overwriting with random data or physically damaging the storage. Unlike sanitization, destruction doesn't require a process to verify total removal. This difference is vital, as there's a risk of exposure without verification.
Data Destruction Regulations
Following industry standards is essential for organizations keen on implementing effective and compliant info removal. The certification serves as formal proof of secure destruction and is critical for audit trails, legal compliance, and maintaining customer trust.
Data Sanitization Certificates
NIST SP 800-88 Certification: verifies that the procedures align with the National Institute of Standards and Technology (NIST) standards. It's a widely recognized standard, especially for government and large-scale corporate entities.
DoD 5220.22-M Certification: is granted when the destruction meets the U.S. Department of Defense criteria. It is predominantly used in the defense and military sectors to prevent data theft.
GDPR Compliance Certification: attests to adherence with the General Data Protection Regulation (GDPR). It's essential for businesses operating in the European Union or handling EU resident's data.

Selecting an Erasure Provider
If your market requires erasure solutions, keep the following key points in mind:
Documentation
Certified erasure services offer detailed records covering the entire deletion process. This should encompass the tracking of custody, a log of the hard drive and data that have been erased, and time-stamped steps for each phase. Such record-keeping enhances transparency and is invaluable for meeting compliance standards and auditing purposes.
Regulatory Adherence
Your chosen provider should adhere to local, national, and international protection regulations pertinent to your industry and location. Whether GDPR in Europe or HIPAA in the U.S., the company ought to customize its offerings to meet specific compliance requirements.
Sensitive Data
A good vendor has sufficient insurance to cover any potential liabilities or risks associated with the erasure process and data breach. Also, evaluate their security protocols, such as employee vetting procedures, transit measures, and fortified facilities, to guarantee that your information is managed with the highest level of confidentiality and will not fall into the wrong hands.
Erasure Techniques
- Software-Based Method: This method uses software to overwrite the storage media with data patterns. It can involve multiple passes to ensure the original showings are irretrievable.
- Cryptographic Erasure: Without encryption keys, old data becomes inaccessible and appears as random characters.
- Block Erase: Specific to flash memory (like SSDs), it erases data in blocks rather than individual files, making it faster than other methods.
- Factory Reset: Commonly used in mobile devices and tablets; restores the device to its original settings. Without additional overwriting, some inputs might still be recoverable.

Legal Requirements
Before you dive into deletion, it's crucial to understand the storage capacity in your devices, whether it's a computer or a smartphone. Each comes with storage components such as SSDs and HDDs. Thoroughly clean these storage units, especially when planning to hand over the handset to a third party. Verification is key; always confirm complete removal. If outsourcing this task, ensure you receive a "Destruction Certificate" as evidence.
Correct disposal is a legal obligation. Laws like Europe's GDPR and the U.S.'s HIPAA dictate secure removal for companies. Following these rules not only protects you from costly data breaches but also favors the environment. Devices that have been securely wiped can often be recycled, cutting down on electronic waste.
While the methods seem straightforward, the execution can be intricate. Accountability during the erasure process is essential, and it can become complex if team members are not aligned. Additionally, while erasure enhances security measures, it may not be eco-friendly if the device itself is discarded.

The Best Data Erasure Software
Searching for a quick and safe method to wipe data from pre-owned smartphones? NSYS Data Erasure has got you covered. This tool is perfect for all kinds of businesses — whether you're a retailer, an online store, a recycling center, a wholesaler, a refurbisher, or a repair shop. It offers a range of benefits, from meeting top security standards to providing certification for each device processed.
Why It's a Top Choice for Businesses:
- Meets Top Security Standards: It follows the rules set by NIST SP 800-88 and GDPR, so you know it's secure.
- Quality: The tool has earned the ADISA certification, which means experts trust it.
- Bulk Erasure: Need to wipe a lot of phones at once? No problem. You can erase up to 60 items at the same time.
- Certified Proof: You get a special erasure certificate for each device processed. For your customers, it shows that you are following the rules and keeping cybersecurity.
One System, Multiple Solutions
Even better, NSYS Data Erasure is part of the NSYS product ecosystem. The list also includes fast, error-free diagnostics solutions, AI grading, accurate pricing, and warehouse management!
In addition to software products, we offer the latest technological development - the Reeva robot, which combines all NSYS tools in one machine. All the data is deleted automatically after cosmetic and functional tests are carried out, and the gadget's price is determined. You get a smooth, all-in-one experience in managing electronic devices — from purchase to resell.
Try Your Go-To QC Assistant
Interested? Let's Talk! If you are on the hunt for a fast, reliable, and cost-effective method to delete data, NSYS is the solution you have been waiting for.
Just drop us a line, and our team will fill you in on all the details you need to know about our solutions!