Sometimes, it's impossible to perform data erasure without a wired connection, for example, if the device is lost or stolen. Also, the remote wipe feature is considered a time saver for businesses that operate with pre-owned devices. But is remote wipe a great way to erase data that provides safe and unrecoverable destruction? Let's find out!
What Is Remote Wiping?
The term remote data wiping describes methods that allow you to delete information from the device distantly without interacting with it directly. Usually, it is done to prevent data leaks when the smartphone is lost or stolen.
This crucial security feature has become increasingly important in our digital age, where data leaks can have significant financial and reputational consequences. The ability to delete stored data remotely offers a layer of protection for both individual and corporate users by ensuring that sensitive information from lost or stolen devices does not fall into the wrong hands.
The most common remote wipe usage scenario is through the MDM profiles. These solutions often provide multiple functions for managing sensitive data on corporate devices. The tools usually include deleting specific files, passwords, accesses, contact bases, or even the complete destruction of all confidential data on mobile devices.
How Does Remote Wiping Work?
Remote wipe functions through software pre-installed or installed on a device, which can be triggered to delete data under certain conditions. Apart from MDM systems, this can be done via various mechanisms, including:
- Web-based interfaces provided by device manufacturers (like Apple's "Find My iPhone" or Google's "Find My Device") where users can log in to a website and initiate a remote wipe if their device is lost or stolen.
- Encryption software that, when a remote wipe command is issued, may not wipe data itself but delete the encryption keys, rendering the data inaccessible.
What Are the Limitations of Remote Wipe?
There are lots of conditions that need to be met so the remote wipe of stored data can be performed:
- The mobile phone needs to be online so you can connect with it remotely.
- This method cannot guarantee the unrecoverability of the information.
- If anyone reloads the mobile device during the remote wipe process, the process won't be fully completed.
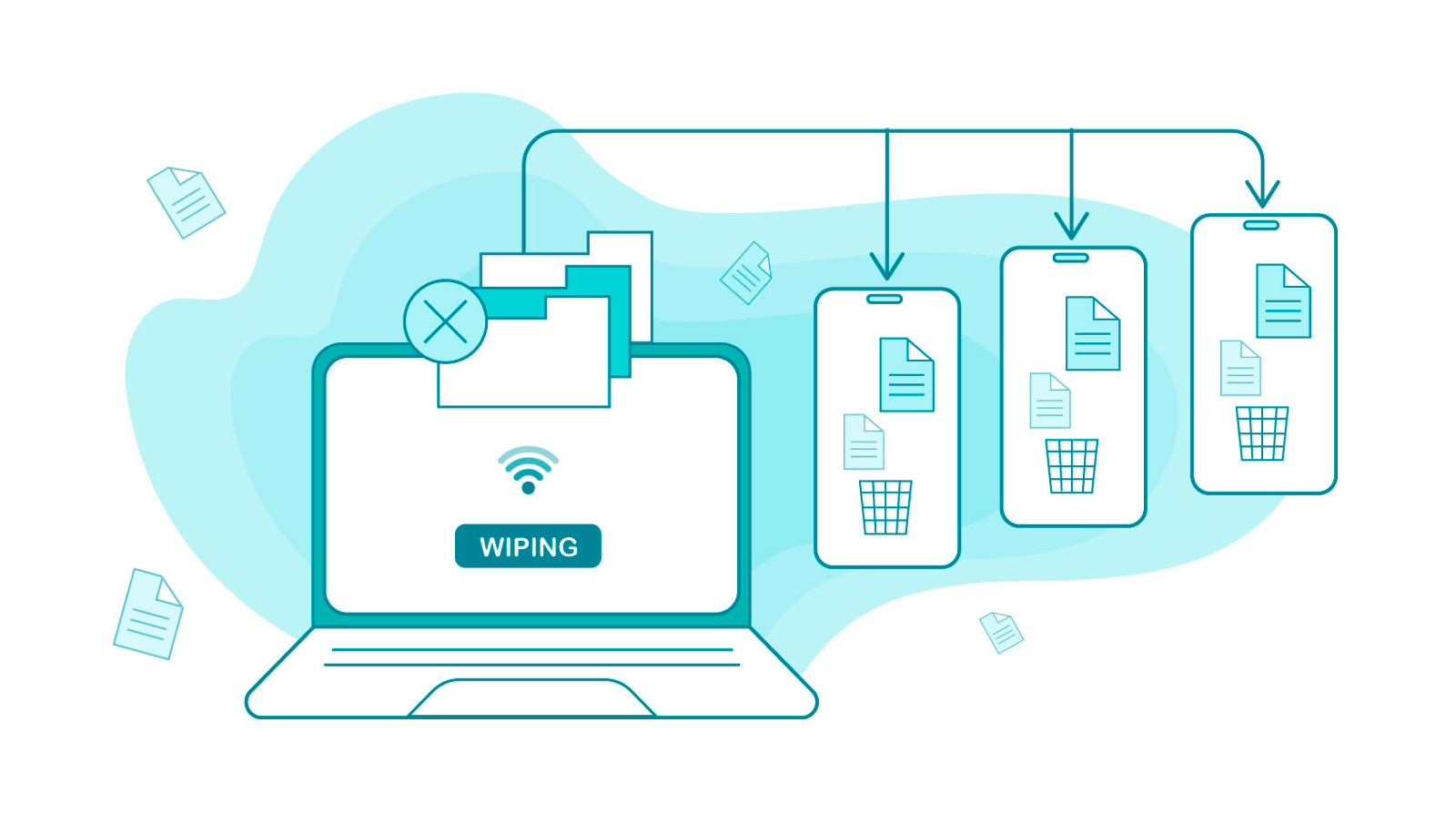
What Are the Benefits of Remote Wipe?
Although there are some significant disadvantages, remote wipes have benefits you should be aware of.
Firstly, it's the ability to delete company-related data in emergencies. If your or your employee's device has been lost or stolen, you can erase all private data from it. This remote wipe method can prevent you from data leakage and be extremely helpful in an emergent situation. However, don't rely on remote wipes as your go-to method; choose other ways to provide data security.
Secondly, the remote wipe is quick and suitable for various types of mobile devices. This mobility is hugely beneficial, especially nowadays when many people work remotely.
How Remote Wiping Can Be Used in the Pre-Owned Device Business?
Used device businesses don't operate with devices that are not physically present at the store or warehouse. However, they are interested in saving time on data erasure, so they might be thinking about remote wiping without connecting mobile devices via a cable.
Is Remote Wiping Effective for Used Device Businesses?
Although wireless data deletion might save you a bit of time, there is a drawback that you need to consider. As the irrecoverability of the deleted data isn't guaranteed, it puts your business at risk of a potential data breach. This risk isn't worth the seconds you save on a remote wipe.
Moreover, a wired connection is required by ADISA standards, so going against it is irresponsible in light of modern data protection norms.
NSYS Group encourages you to use remote wiping only if it's justified in the exact case. Connect with your data erasure software provider to get advice on managing data destruction effectively and responsibly.
What Are the Best Practices for Data Protection?
To avoid using this emergency method, pay attention to the data protection practices that can be implemented to prevent data leaks and maximize mobile security.
These practices encompass a range of strategies and technologies designed to protect data across all stages of its lifecycle.
- Implementing strong encryption for data at rest and in transit ensures that even if mobile device data is intercepted, it remains unreadable to unauthorized parties.
- Regularly updating and patching software and systems eliminate vulnerabilities that could be exploited by cyber attackers.
- Employing comprehensive access controls, such as multi-factor authentication (MFA) and the principle of least privilege, ensures that only authorized users have access to sensitive corporate data and only to the extent necessary for their roles.
- Regular backups of critical data, stored securely and tested frequently, are essential for recovery during data loss or a ransomware attack.
- Additionally, educating employees about cybersecurity best practices, including recognizing phishing attempts and safe internet browsing habits, creates a culture of data security awareness that acts as the first defense against cyber threats.
- As previously discussed, the use of Mobile Device Management (MDM) systems and policies for remote wipes play a crucial role in the secure management of mobile devices and the protection of associated data contained within them.
Together, these security features and practices form a robust framework for mobile security and data protection, helping to prevent data breaches and ensuring data confidentiality, integrity, and availability.
But How to Save Time on Data Erasure?
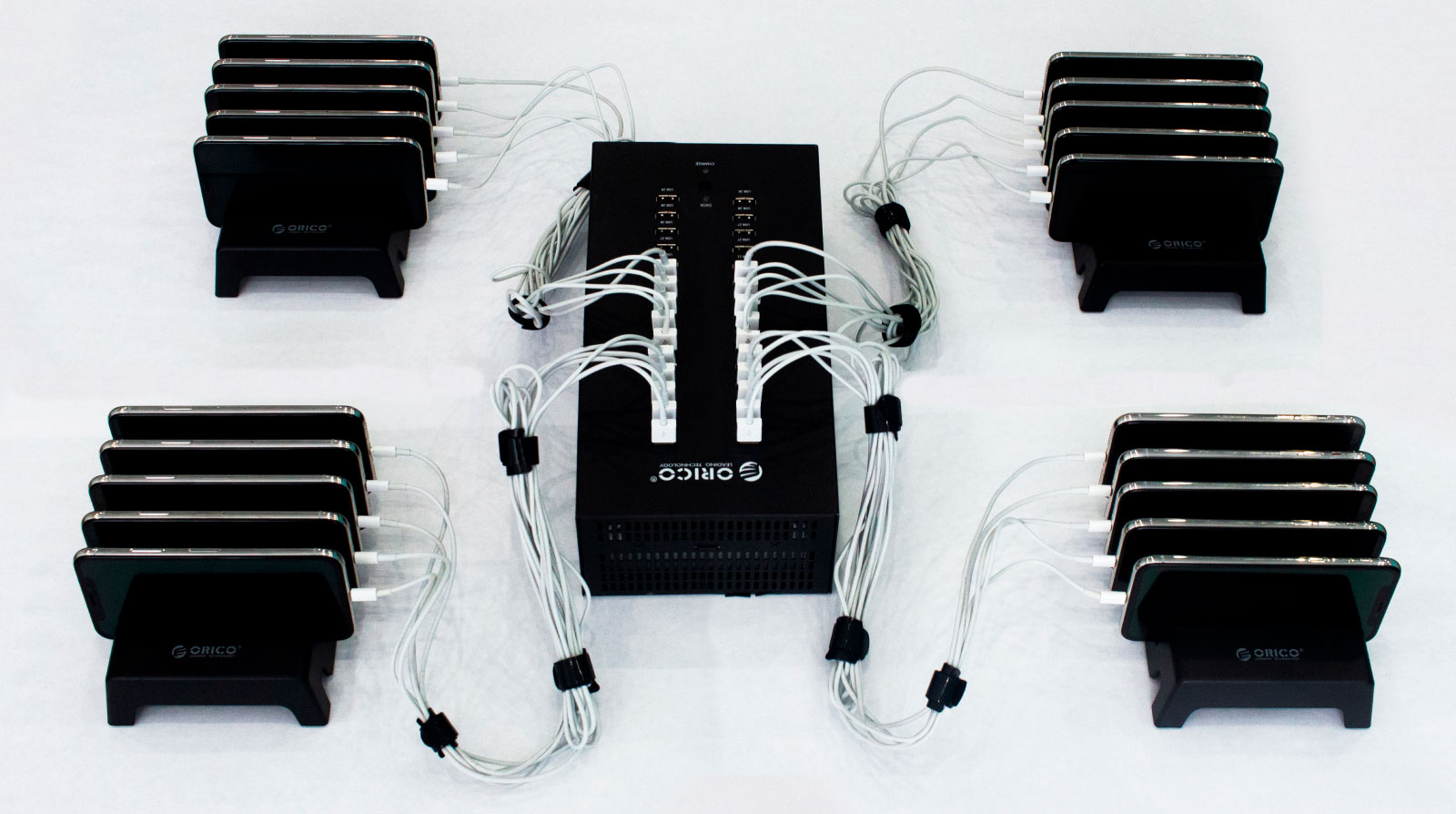
Instead of going for remote data wiping, try simultaneously erasing information from several devices. NSYS Data Erasure provides this functionality: you can connect up to 60 devices at once! After every erasure made, you will get a detailed report to prove that confidential data was deleted irrecoverably in accordance with international standards.
NSYS Data Erasure is certified by ADISA and compliant with GDPR and NIST SP 800-88 attribution.
Click the button below to arrange a demo!








